This tutorial is about installing OpenVPN server on a CentOS server and setting up the client and drivers to work with Windows 7.
Installing OpenVPN on server:
We begin by logging in to your server control panel and making sure TUN/TAP service is enabled, for some providers you might have to write them a ticket requesting it to be enabled. Then we log in and download the openvpn package with the wget command:
wget http://pkgs.repoforge.org/rpmforge-release/rpmforge-release-0.5.3-1.el6.rf.x86_64.rpm
Next, we install the downloaded package with sudo rpm:
sudo rpm -Uvh rpmforge-release*
Notice how I replaced the rest of the file name with * its easier then typing out the whole name,we could also write rpm and press tab to autocomplete the file name.
Then we type sudo yum install openvp openssl-devel -y
You should see a bunch of files download and install which is what we want:
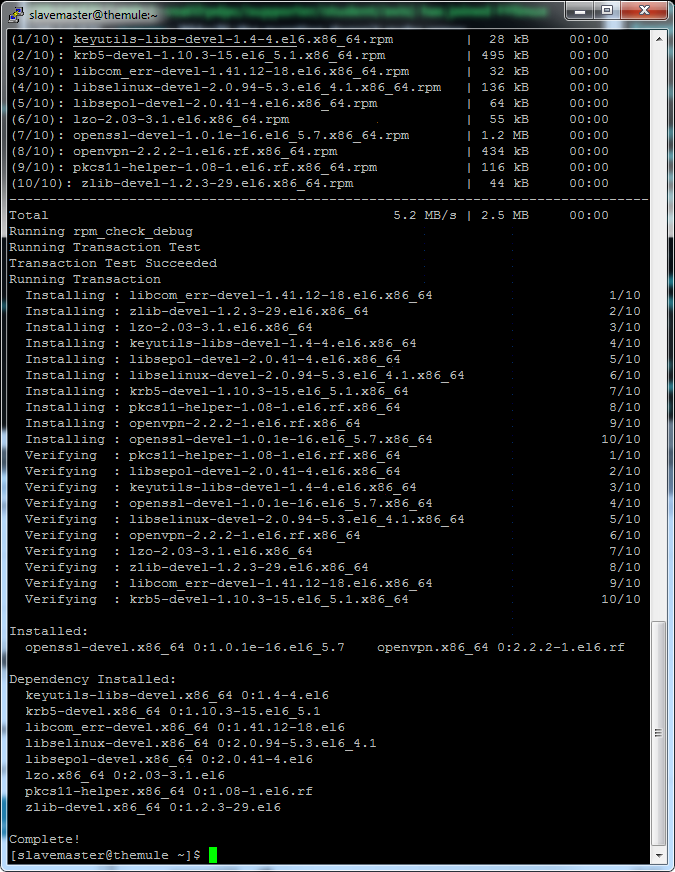
Now we have to copy the key building folder to /etc/openvpn
sudo cp -R /usr/share/doc/openvpn-2.2.2/easy-rsa/ /etc/openvpn/
We now have to edit the vars file in the easy-rsa folder with some text editor, i use 'nano':
sudo nano /etc/openvpn/easy-rsa/2.0/vars
We need to find a line called
export KEY_CONFIG='$EASY_RSA/whichopensslcnf $EASY_RSA'
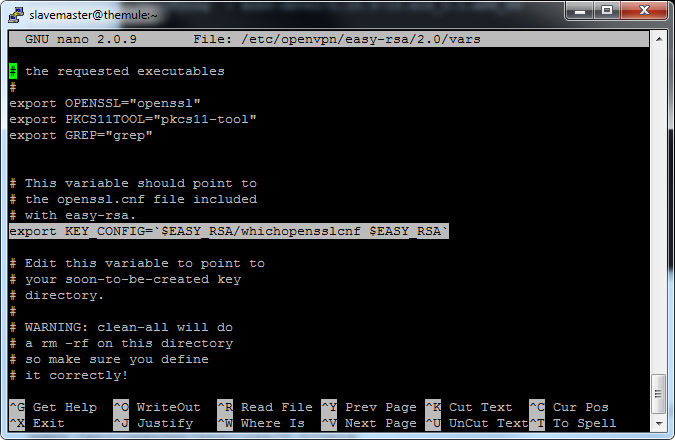
and replace it with:
export KEY_CONFIG=/etc/openvpn/easy-rsa/2.0/openssl-1.0.0.cnf
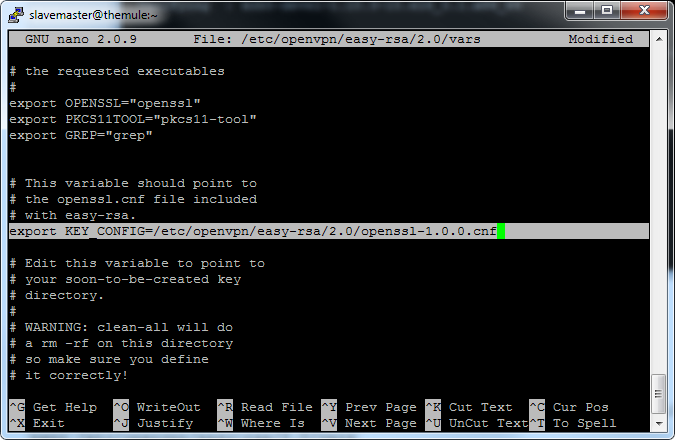
then save and exit.
Now we have to make the certificates for the server and the client. We firstly go to the 2.0 folder in the easy-rsa folder we moved earlier:
cd /etc/openvpn/easy-rsa/2.0
and then we give the 2.0 folder read, write and execute permissions:
sudo chmod 755 *
Then we do the following:
source ./vars
./vars
sudo./clean-all
And then we start building the certificate authority:
sudo ./build-ca
for some reason the above command didn't work so i switched to root with su root and tried ./build-ca again and it worked, launching a little questionnaire for you to answer you can put it any answers you like except the 'Common Name'. Use your hostname to answer this one.
Now we can generate keys for the server:
./build-key-server server
This will launch yet another set of questions, when you're asked for common name use 'server' and leave challenge password blank and then sign the certificate.
Then we have to ./build-dh to build a Diffie Hellman whoever he is.
And now we can make a new server config file with the touch command for creating new files:
sudo nano /etc/openvpn/server.conf and enter this in there:
port 1194 #- you can use whatever port you like 1194 is the default
proto udp #- this is the protocol you will be using
dev tun
tun-mtu 1500
tun-mtu-extra 32
mssfix 1450
reneg-sec 0
ca /etc/openvpn/easy-rsa/2.0/keys/ca.crt
cert /etc/openvpn/easy-rsa/2.0/keys/server.crt
key /etc/openvpn/easy-rsa/2.0/keys/server.key
dh /etc/openvpn/easy-rsa/2.0/keys/dh1024.pem
server 10.8.0.0 255.255.255.0
push "redirect-gateway def1"
push "dhcp-option DNS 8.8.8.8" #-this is your dns addres
push "dhcp-option DNS 8.8.4.4"
keepalive 5 30
comp-lzo
persist-key
persist-tun
status 1194.log
verb 3
The last thing before starting the server is to apply the corret routing rule so that the traffic from the windows client is passed through to the server and then out to the internet:
/sbin/iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -j
After you're done you can close and save this and start openvpn with
service openvpn start command and the make sure openvpn starts on boot with chkconfig openvpn.
Then we go to the 2.0 folder in /etc/openvpn/easy-rsa/2.0 to make the 1st client key, for me this command only worked as root so i did su root and then ./build-key client
This will bring up another set of questiosn like with the previous certs, answer them any way you like, the less true information you give the more privacy you have I suppose.
Next, we can enable ipv4 routing by editing the config file sudo nano /etc/systclt.conf and changing
net.ipv4.ip_forward = 0 to net.ipv4.ip_forward = 1 0 means off 1 means on.
Client Side Setup:
Now that we have our client key ready we can install the OpenVPN client for windows from here
When installing make sure that Tap Virtual Ethernet Adapter, OpenVPN GUI and Depenedcies are ticket:
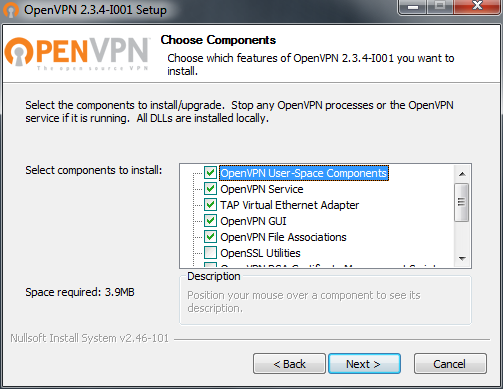
then just click next and say yes to everything.
Then we need to make the client config file so go to C:\Program Files\OpenVPN\config and make a new text file called whateveryoulike.conf and paste this in it:
client
dev tun
proto udp
remote x.x.x.x 1194 # change x.x.x.x to your servers ip and port to your VPN port
resolv-retry infinite
nobind
persist-key
persist-tun
comp-lzo
verb 3
<ca>
Paste the contents of ca.crt here
</ca>
<cert>
Paste the contents of client.crt here
</cert>
<key>
Paste the contents of client.key here
</key>
And replace all the text that needs replacing whith the content of the client flies found in /etc/openvpn/easy-rsa/2.0/keys. Once thats done launch the OpenVPN GUI Right mouse click the icon select your name and click connect!
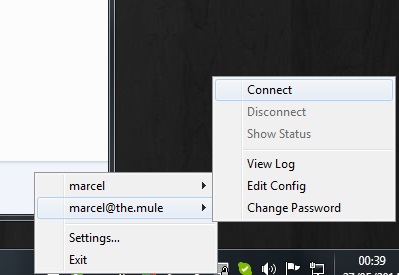
To test if its working just google 'my ip' and it should return you your servers IP.
:)
