Hello, in this short tutorial I'll show you how to secure a Linux server so that its slightly more secure and safe from any kind of bots or automated attacks.
SSH:
If your SSH is listening on it's default port (22) its like leaving the keys to your house under the door mat, its the first place any potential thief would look at. Because of this crawlers and bots can be programmed to explore the interwebs and try to connect to your servers IP and default port and attempt to log in. If you go to var/log/secure* you will see hundreds if not thousands attempts at logging in as root user, its the most common username.
Having the most common username and port enabled means that you just made the thief’s job easier because now he knows where the key is, where the lock is but he doesn't know which key it is. So to make things more secure we need to change the default ssh port. To do this all we do is go to the sshd config file located at /etc/ssh/sshd_config find the line wich contains #Port 22 in it and uncomment it by removing the # . Uncommenting basically tells the server that this specific config line is not default anymore and should be read to see what changed, in this case the port number.
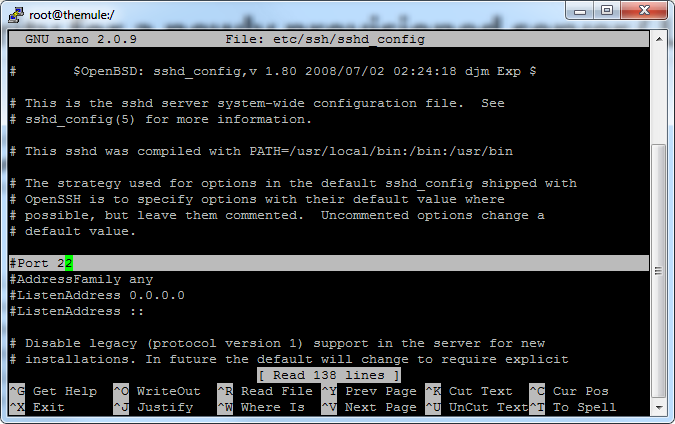
Then change the port to whatever number you like except common ports such as 22,23,80,443, etc because they are obviously common used by other services.
Make sure you remember this port because if you don't you will be locked out.
If you didn't know this you are trying to run before you can walk!
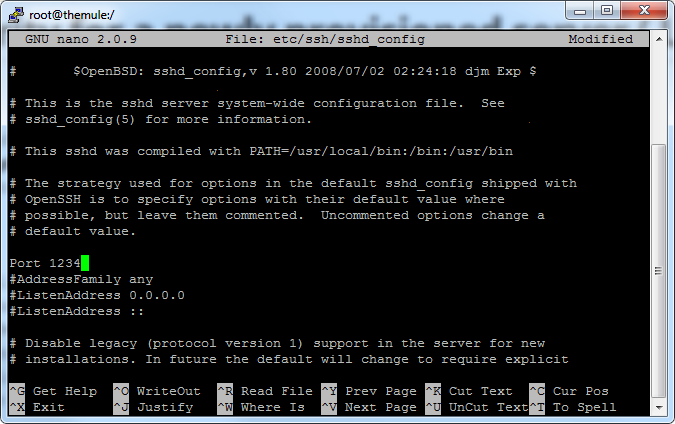
Once that’s done you can save and exit the file editor and restart the SSH service by typing service sshd restart you should see two messages with [OK] in in them which is all we care about. If you see [FAILED] its self-explanatory, go back to the config and look for any mistakes.
Once you completed all of the above close your current SSH session and change the port number in your client to the one you just put in the config file and save.
Disable root user and grant root privileges to a new user:
Disabling the root user improves the security of your server because just like changing the default SSH port we change the default username. Firstly, we create another user, grant it certain root privileges that will be enough for 99% of operations we ever have to do, and then disable the real, unrestricted root user so that when the other user is hacked we still have the option of enabling the unrestricted root user and having total control of the server.
First off, we log in to the server as root and create a new user with the following command
adduser username
Then we set a password for the newly created user:
passwd username
we will then get prompted to type our password, make sure its difficult and you remember it.
Next, we give the user root privileges, by opening the config file with following command:
sudo /usr/sbin/visudo
we then scroll down the pages of the config file using PageUP and PageDown buttons until we see a line which looks something like this:
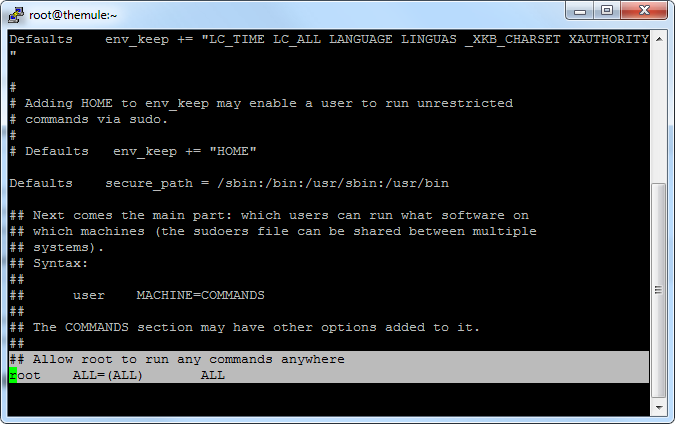
Then we add our new username under the root line using arrow keys to navigate to the space and pressing i.Thenu copy the rest so it looks like this:
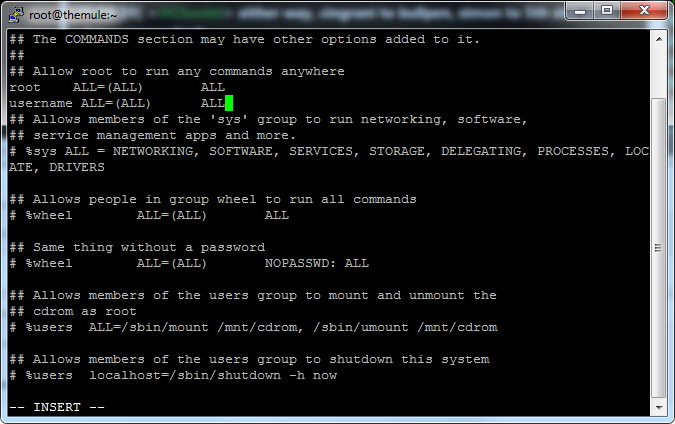
We then exit the editing mode by pressing escape , pressing the : button and typing wq and hitting enter. WQ means write and quit in case you wondered.
Then we add the new user to the wheel group by typing usermod -G wheel username to give it root-like power and let them run sudo commands by default. From now on we can install and do things just like we would with root user but instead of typing yum install something we will have to type sudo yum install something.
To disable the root user login via ssh we edit the /etc/ssh/sshd_config file by uncommenting it and changing the line saying PerminRootLogin from yes to no and restart ssh with service sshd restart. If you now try to log in as root and enter the password you should be greeted with Access denied message :)
IPTABLES:
IPtables is a basic firewall for linux systems with which we can allow or block connections and open/close ports. By default when your VPS deploys your server it comes with no firewall at all or a not configured firewall meaning all ports and connections are opened.
So to begin, we install iptables with sudo yum install iptables command.
And now we can add a few basic rules to block bots trying to port scan us.
First command being: (be careful when typing these commands as they are case sensitive)
One of the simplest things we can do to improve the security of our server is to close all the ports except the ones we use.
So we begin by doing:
sudo iptables -P INPUT DROP which drops all the input aka incoming traffic.
Then we make sure that we didn’t close localhost by typing:
sudo iptables -A -i lo -p all -j ACCEPT
Then we open any ports we might need with:
sudo iptables -A INPUT -p tcp -m tcp --dport yourport -j ACCEPT
I would advice that you open your SSH port first then exit and reconnect to make sure it worked. Then you can open all the other ports your services need.
The last thing that i know of we can do is close a port, for example your SSH to all IP's except yours, this is great if you are connecting with a VPN or you have a static IP address, if you have a dynamic one and it renews, it will lock you out.
So to do this we type the following:
sudo iptables -A INPUT -p tcp -s your ip -m tcp --dport yourport -j ACCEPT
Then, we save iptables configuration we type iptables -L -n which will save any changes made and give you a list of them.
That’s it for now!
